Search
Welcome!
This blog is used to collect useful snippets related to Linux, PHP, MySQL and more. Feel free to post comments with improvements or questions!
Are your smart devices spying on you? Make better purchasing choices and find products that respect your privacy at Unwanted.cloud
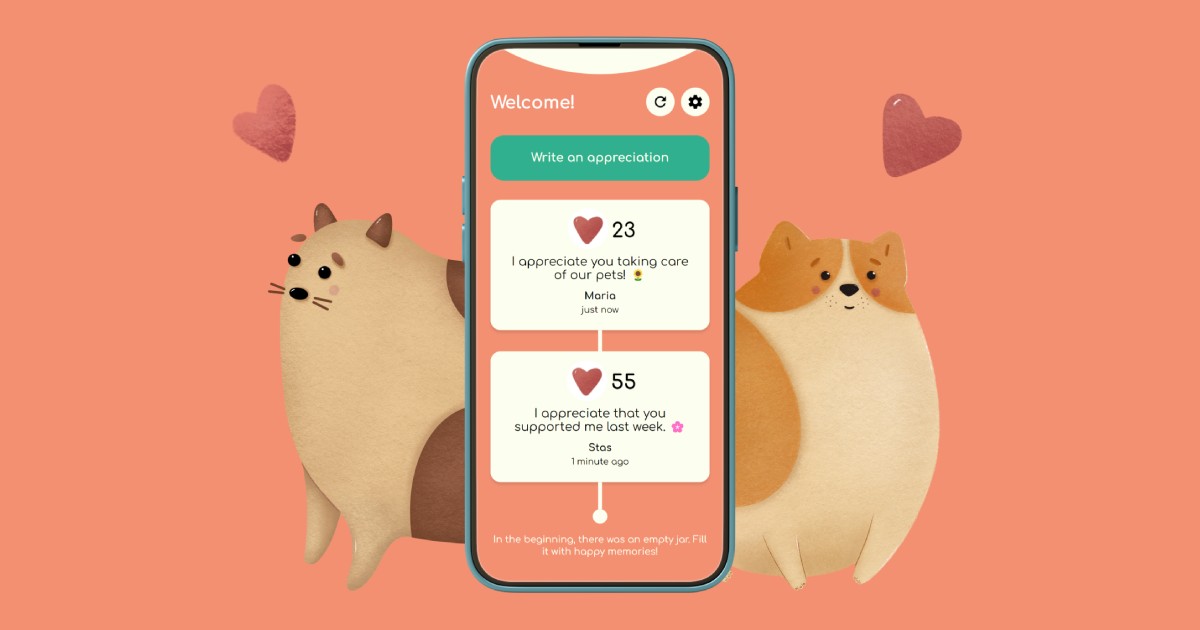
Appreciation Jar
I recently launched the Appreciation Jar app. It is a gratitude journaling app for couples. Try it here!
Popular post
 Preconfigured Airplay speaker (Shairport) – Downloadable Raspberry Pi image
Preconfigured Airplay speaker (Shairport) – Downloadable Raspberry Pi image
Download a preconfigured image for the Raspberry Pi that allows you to use the Pi as an Airplay speaker!
Copyright © Useful Snippets. 2025 • All rights reserved.
Cedar WordPress Theme by EckoThemes. Published with WordPress.